
Cyber threads for companies
How long can your company function without IT? In today’s digital world, cyber damage can quickly become an existential threat. What are the risks in the cyber world, and how can companies arm themselves against attack?
Even attacks from the child´s room are possible
It often remains unclear who initiates these kinds of attacks. In the case of some attacks, international criminal organisations are suspected of having their own ‘digital department’ and infecting targeted companies with malware. In other cases, whole governments are the suspected culprits, spying on companies in other countries and obtaining sensitive information. As a current situation in Germany at the turn of 2018/2019 has shown, however, it does not have to be a criminal organisation or government secret service behind a data scandal. A school pupil managed to access sensitive data of politicians and prominent individuals right from his bedroom. Obviously awareness of cyber risks is still not high enough even several years after the scandal involving Angela Merkel’s mobile phone. In light of this, one dreads to think who might be hidden in company networks, silently and secretly creeping about undetected. There are certainly plenty of parties interested in information about patents, technical drawings, customer and supplier relations, pricing strategies, market shares, profit margins and much more.
‘Nothing functions without IT. IT failures mean that individual departments or even the entire business is shut down.’
When business comes to a standstill
The IT infrastructure today represents the central nervous system of any company. As such, individual machines are connected through IT, and the entire production and logistics processes are interconnected as well. The same applies to many other subsystems in the company. ‘Nothing functions without IT. The failure of these intricate, permanently interwoven network structures inevitably means that individual departments or even the entire business is shut down,’ says Hendrik F. Löffler, Member of the Funk Management Board. ‘Failure scenarios lasting from just a few minutes and hours or even days and weeks are possible.’
Even when companies have seen the signs of the times and installed high-quality protective mechanisms, no company is completely protected against cyber damage. After all, companies do not only have to arm themselves against attacks from the outside. As Löffler says, ‘Carelessness and negligence amongst a company’s own employees or just plain mistakes in operation can lead to IT failures – causing the entire business to come to a halt.’ As far as a company’s balance sheet and profit and loss statement are concerned, it is completely irrelevant whether damage comes from internal or external sources. As conventional business interruption insurance policies very rarely cover this type of damage, companies often remain exposed to the costs of such events.
IT alone cannot overcome these challenges
What precautions can companies take? Naturally IT departments protect their own systems as best they know how to with the options available. Nevertheless, their solutions usually only focus on the IT itself and do not consider company-wide value creation contexts. In many cases, huge cyber risks only first arise from the interdependencies between the individual company departments, meaning that the IT department cannot come up with a holistic damage calculation on its own. For example, expertise from Controlling and Production would be essential in order to assess the extent of lost profit margins for a certain product line in the event that the ERP system goes down for five days. Even the causes of damage often do not fall anywhere within the IT department’s sphere of influence: for example, an employee in Production may cause great damage by importing a machine software update incorrectly. Or the external machine supplier may inadvertently infect the production network with a virus when performing remote maintenance.
Are you prepared if this happens to your company?
Cyber risk remains a hot topic and will not be disappearing from the daily agenda in the foreseeable future. Even more alarming is the result of the 2018 Cyber Security Report: in one out of three companies, the executive board does not spend any serious time – if any at all – considering cyber security, and usually only really thinks about it when an incident occurs. Do you know your company’s cyber risks? Do you know what implications the many different risks may have for the success of your business? A specific risk analysis can give you more transparency and a better understanding of your risk. It is therefore an important step for effective cyber risk management.
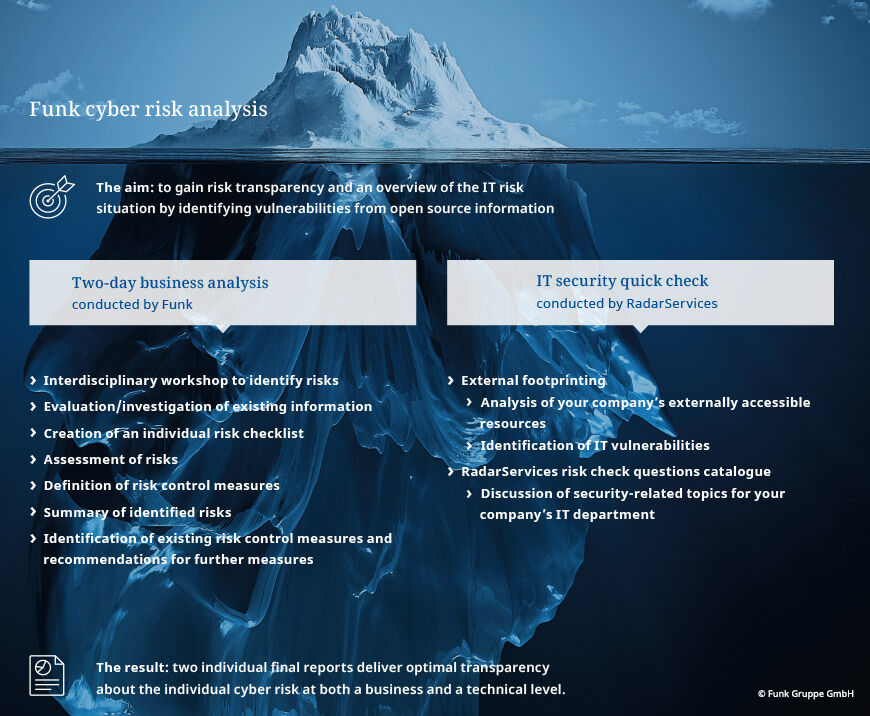
A Workshop illuminates processes within the company
Funk offers an individual analysis as part of an interdisciplinary workshop. During preparation the project objectives and the associated project team are defined in binding terms. To represent all company departments, usually the heads of Purchasing, Controlling/Finance, Sales and Production, as well as the insurance and risk management teams, all take part in the risk analysis along with the head of IT. The participants work with the experts from Funk as they discuss possible risk scenarios along the value creation chain and prioritise the risks. Using a business impact analysis, the existing processes in the company can be assessed in connection with the risks and their severity. In this analysis, all risk fields, existing measures, interdependencies and downtimes are taken into account, to create a transparent picture of the current risk situation and of the interdependencies between IT and analogue value creation. If desired, a penetration test from our exclusive cooperative partner RadarServices can be used to provide a concrete look into the actual existing IT security vulnerabilities. According to cyber expert Löffler, ‘With the Funk cyber risk analysis, companies not only get increased risk transparency but also a strong basis for insurance solutions.’ The data gained from the analysis can also be used to create contingency or business continuity plans. As a result, while cyber damage will always be problematic, it is no longer an existential threat.
04/11/2019
Your point of contact


